HTTPS runs on transport layer of TLS on port 443. The predecessor of TLS was SSL, which deprecated.
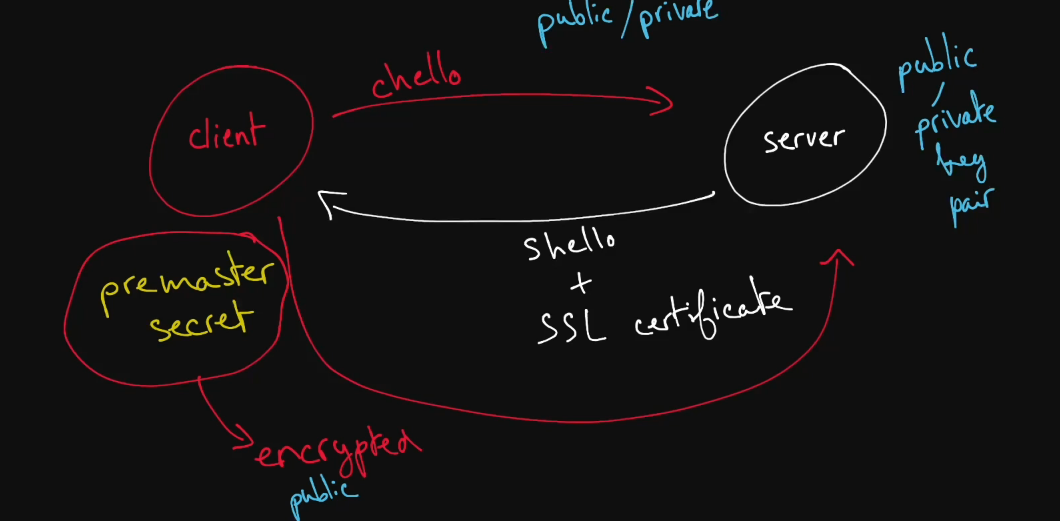
- TLS handshake issued by the client, let’s call the message ‘chello’ for simplicity.
- The server responds with shello + ssl certificate (including the public key of the server).
- The client obtains the server’s public key, which is piggybacked to the certificate.
- OCSP, also known as verifier, will validate this certificate.
-
The client generates pre master secret, which a bunch of random bytes.
-
Using chello, shello, and the premaster key, the client will generate session keys (Symmetric Key), encrypt with the server’s public key, and send it back to the web server as a message.
-
It encrypts the pre master secret and sends it to the server using the extracted public key.
-
Using the server’s private key, the server will be able to decrypt this secret.
Only the server will be able to use this session key, and it will be used only during the session, so once their session ends, they will never use it again.